Microsoft Enterprise Mobility and Security
 Author, Dimitri Dizna
Author, Dimitri Dizna
CEO, BINARC
Microsoft created the Enterprise Mobility and Security (EMS) in March 2014. This product was designed to shift to built-in security, as opposed to bolted-on security. The EMS was created to help provide high-level security to small and medium-sized businesses. Microsoft EMS is most frequently used by IT specialists responsible for setting up network security, employee authorizations, devices, and more. EMS can also be set up and configured by a Microsoft Partner when necessary. Microsoft’s EMS can seem confusing at first, but once its components are broken down, it can be much easier to understand.
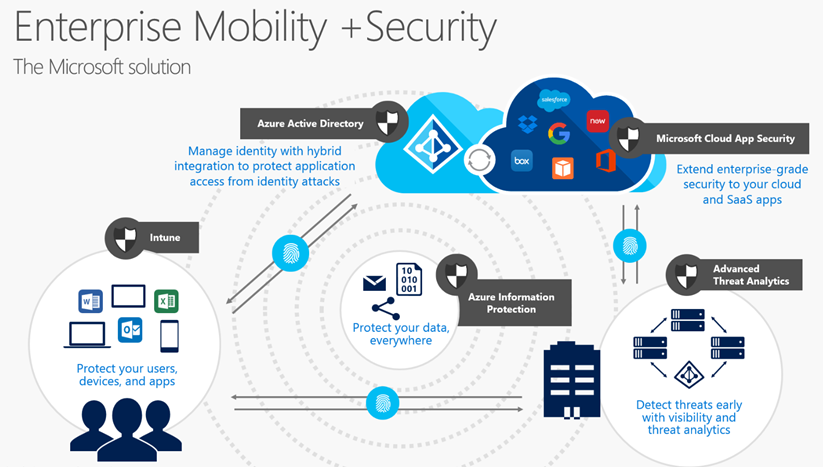
The Microsoft Enterprise Mobility and Security product comprises six individual components that have their own features. These applications support mobile device and app security, and privileged and conditional access. They include advanced security reporting and multi-factor authentication. Products in the Microsoft Enterprise Mobility and Security system include:
- Microsoft Intune device management,
- Microsoft Identity Manager,
- Microsoft Cloud App Security,
- Azure Information Protection,
- Azure Active Directory, and a couple of other supporting applications.
Identity and Access Management
Azure Active Directory Identity Protection
Azure Active Directory Identity Protection is included in the Azure Active Directory Premium P2 plan, which comes with the Enterprise Mobility and Security E5. The Azure Active Directory runs in the background of Office and Microsoft 365, meaning it’s hardly even noticeable. This technology is responsible for managing the identities of employees. In simpler terms, it’s the system that checks the login credentials for users. There are two different Azure Active Directory licenses available to choose from with the Microsoft Enterprise Mobility and Security. The EMS E3 is equipped with the Azure Active Directory Premium P1, while the EMS E5 features the Azure Active Directory Premium P2.
Azure Active Directory does more than standard reporting tools; based on risk events, it estimates the risk level for each individual user. The Azure Active Directory provides each employee with a profile in the directory, which links to all their other user logins. This allows users to sign into services regardless of the device’s location, model, or the user’s identity. It includes access to services including email, file servers, applications, and data. Another great feature is conditional access, which can block specific users from logging into systems based on various factors. The single login feature is available for all devices, including Android and iOS, while a multifactor authentication is utilized to help verify identity through biometric scanning or SMS verification. The Azure AD has simple, easy-to-follow instructions and has an overall quick setup process.
Azure Active Directory Privileged Identity Management
Azure Active Directory Privileged Identity Management is included with the Azure AD Premium P2, which is available with the Enterprise Mobility and Security E5. Accounts with full privileges can present a risk, as these accounts are more likely to be targeted for attacks. The Azure AD Privileged Identity produces immediate access to administrators when needed and regular access the rest of the time. Through this feature, the Azure Active Directory administrators are enabled to get administrative reports and access history, as well as any changes to the administrator’s information or assignments.
Device and Application Management
Microsoft Intune
Microsoft Intune is built on the Azure Active Directory and provides security between employees’ devices and the companies personal data. It allows users to link a limitless number of mobile devices to the Active Directory profile for employees. For example, employees can use Microsoft Intune to download the Microsoft Word application and access their companies documents securely from their mobile devices. The IT department of a company can also use Microsoft Intune to block access to specific users, as well as data, devices, and specific applications. Another important advantage given by Microsoft Intune is that employees aren’t required to provide the IT department complete control over their devices for secure access to data.
Microsoft Intune offers businesses full control over their company’s data. It secures files, helps keep up to date on anti-malware software, and fixes other issues by setting and monitoring the companies policies. Some of the other things that can be done with Microsoft Intune include managing the mobile devices and applications used by employees to access data. It also helps to protect businesses information by providing control over the information that employees see and share.
System Center Configuration Manager
Microsoft Intune is a subscription-based service. It is licensed per user per month, with a maximum of 5 devices per user. The Microsoft System Center Configuration Manager is an extensive platform designed to manage devices while the system’s features include software arrangement, updates, inventory, and reporting.
Information Protection and Security
Microsoft Advanced Threat Analytics
Microsoft Advanced Threat Analytics provides real-time monitoring to provide security. Microsoft EMS is primarily stored in the cloud, where all types of standard data are collected. This means that Microsoft EMS logs every document, location, device, user, access request, and more. These logs are then processed and analyzed to identify any patterns or signs of suspicious activity.
Microsoft Advanced Threat Analytics is based on machine learning, so it’s always on and constantly improving. If it detects a threat or other issue, Microsoft EMS gives users recommendations regarding best ways to fix the problem.
Azure Advanced Threat Protection
Azure Advanced Threat Protection helps to protect hybrid IT environments by utilizing on-site security to detect and analyze advanced threats, malicious actions, and compromised identities before they can cause any damage to your company. Azure ATP uses learning-based analytics to monitor users’ behavior and activities and protects users’ identities and data stored in the Active Directory. It also detects and checks into suspicious user activities and provides clear incident information for a simplified timeline and report.
Azure Information Protection
Azure Information Protection helps users’ identify sensitive data. Microsoft software is intelligent in doing this, meaning it can easily identify information such as social security and credit card numbers. Custom rules can also be set by the IT department on how to identify this sensitive information and label it as sensitive, or secret, so different protection rules and policies will be applied.
Azure Information Protection helps protect users’ documents and emails, helping to ensure that only the intended recipients can view the items sent to them. Even if the documents are forwarded or saved by someone else, even on a flash drive, no one else will be able to access them. Azure Rights Management (RMS) can encrypt documents and protect them. This protection remains with the document, and access is verified each time it is opened. Access can also be tracked and revoked. With the Azure Information Protection client, policy-driven labels can be applied to documents to classify different types of data, such as public, general, and confidential.
Azure Rights Management
The Azure Rights Management is “document-level” security. With this, every time protected data is accessed, a check is done to verify that the person viewing the data is allowed to do so. Users can be blocked based on several reasons including employment status, which can remove access for terminated employees. Other reasons can include the position in the company, the active directory information, and much more. Azure Rights Management is included in the Office 365 system, so users won’t notice it unless they’re trying to access something that they aren’t verified to.
Microsoft Cloud App Security
The Microsoft Cloud App Security tool is a Cloud Access Security Broker, that configures how data travels and allows visibility into security threats that may arise. This Shadow IT helps identify the cloud apps, PaaS, and IaaS services used by your business. The app security also detects and investigates usage patterns, estimates risk levels, and assesses the business’s readiness of over 16,000 SaaS apps against over eighty risks.
Protecting against anomalies and online threats is done by detecting uncommon behaviors across the cloud apps and identifying malware or compromised applications. Sensitive information is protected anywhere in the cloud with policies in place, and strict processes followed to monitor these policies in real-time. The Microsoft Cloud App Security also evaluates and verifies that cloud apps meet all the compliance requirements in place, preventing data from leaking out to non-compliant apps.
About Us
BINARC is a Microsoft Managed Services Provider that has utilized best-in-class people and tools to solve complex IT challenges for more than 20 years. We deliver customized IT solutions to drive digital transformation and improve efficiency, security, and remote work capabilities for clients large and small in both the public and private sectors.
For more, contact us by phone at 202-681-7787 or online. You may also schedule a free 30-minute IT architecture strategy session via our online booking tool.


